In today’s fast-paced DevSecOps world, even small oversights can lead to significant vulnerabilities. What if you could avoid bigger mistakes by mastering a few fundamental security constructs? This article breaks down the basics of SELinux, SecComp, Namespaces, and Control Groups (cgroups)—essential tools that can safeguard your Kubernetes clusters and protect your systems from cybersecurity attacks.
Why should you care?
Because understanding these simple yet powerful constructs isn’t just for security experts—it’s for anyone managing containerized environments or Kubernetes clusters. These hands-on practices can help you:
- Isolate processes to minimize risks.
- Control and limit system resource consumption to avoid container sprawl.
- Define what a process or container can and cannot do, reducing attack surfaces.
In this article, you’ll learn:
- How SELinux enforces access controls and protects processes?
- Why SecComp is your go-to tool for restricting system calls?
- How Namespaces isolate resources to ensure better boundaries and security?
- The role of Control Groups (cgroups) in managing system resources effectively?
Whether you’re just getting started or looking to reinforce your Kubernetes clusters against potential attacks, these foundational principles are must-haves in your security toolkit.
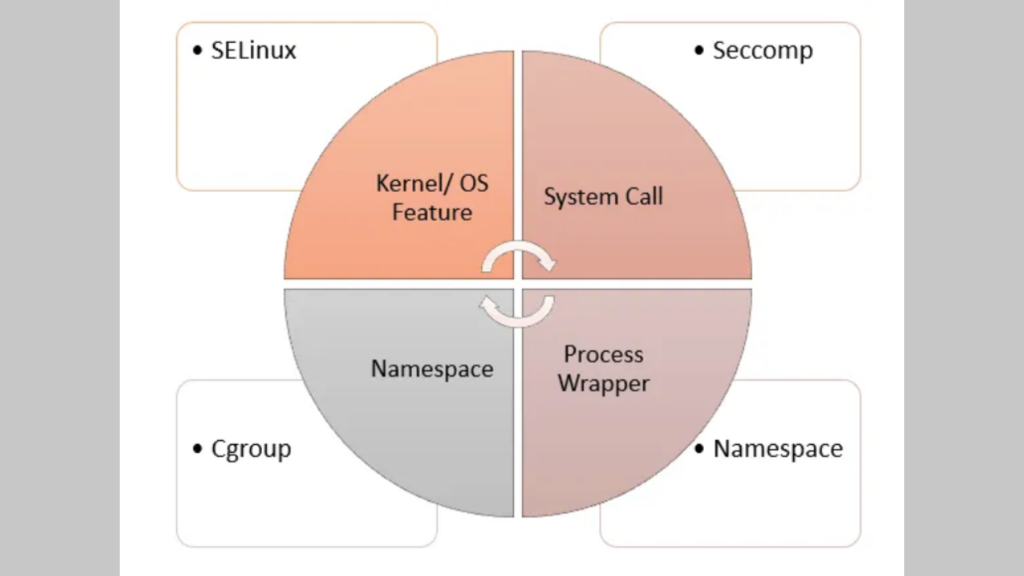
SELinux
SELinux (Security-Enhanced Linux) is a mandatory access control system for processes. Linux kernel uses SELinux to protect processes from each other and to protect the host system from its running processes. Processes run as a confined SELinux type that has limited access to host system resources.
Condition that brings SELINUX into action. Check or configure file /etc/selinux/config for possible SELINUX values:
- SELINUX=disabled or
- SELINUX=enforcing or
- SELINUX=permissive
Seccomp
Seccomp stands for secure computing mode.
The seccomp() system call operates on the Secure Computing (seccomp) state of the calling process.*Man page definition
Seccomp limits how processes could use system calls. Seccomp defines a security profile for processes, whitelisting the system calls, parameters and file descriptors they are allowed to use. SecComp defines which system calls should and should not be allowed to be executed by a container. It restricts the calls a process/continer able to make from userspace into the kernel.
Namespaces
The kernel can isolate specific system resources, usually visible to all processes. This is done by placing the resources within a namespace. Inside a namespace, only processes that are members of that namespace can see or utilize those resources. Namespces help apply security restrictions to containers. Below mentioned are major 7 namespaces that help achieve boundaries and restrictions:
- Cgroup — Cgroup root directory
- IPC — Inter Process Communication, POSIX message queues
- Network — Network devices, stacks, ports, etc.
- Mount — Mount points
- PID — Process IDs
- User — User and group IDs
- UTS — Hostname and NIS domain name
Control groups (cgroups)
Control groups partition sets of processes and their children into groups to manage and limit the resources they consume. Control groups place restrictions on the amount of system resources that processes can use. Those restrictions keep one process/container from using too many resources on the host.
- CGroups Examples:
— cpu-shares
— cpuset-cpus
— memory-reservation
— kernel-memory
— blkio-weight (block IO)
— device-read-iops
— device-write-iops
Hands-On Example and Learning Opportunity
If you’re eager to see these principles in action, don’t miss the DevSecOps Hungary session recording, where I dive into these concepts and even demonstrate a live hacking demo of a real system. Watch it here: DevSecOps Hungary Recording.
1 Comment
Gabby
March 11, 2023Good refresher!